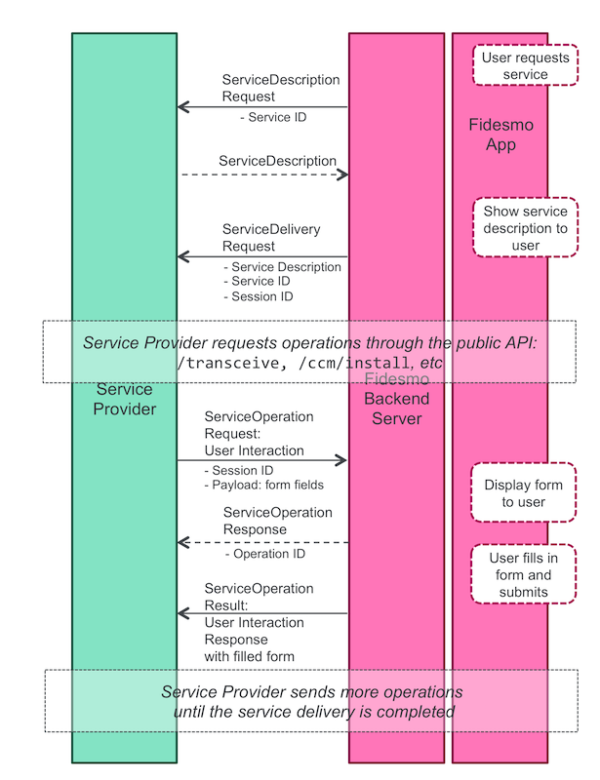
A user interaction request is composed by an array fields. Each element of fields is described in the following table:
Fields inside a request| NAME | DESCRIPTION | TYPE |
|---|
label | The text label that will appear together with the system UI component defined by the type field. Multilanguage is supported. | Dictionary |
id | The id used to identify this field | String |
type | The type of UI control that the user will see in the Fidesmo App | String |
format | Provides an extra information about how the UI control will be rendered or what kind of data it will support. The format is optional and if not supplied or an unknown format is used the field falls back to the default. | String |
And finally, this is the list of type and format supported:
Supported data type and format| NAME | TYPE | FORMAT | DESCRIPTION | LABEL | RETURNS |
|---|
| Input text field | edit | text | Shows a text input. Default if format is not specified or not supported. | The label that should be shown above the text input supplied as a Dictionary. | The user input as a string or an empty string if nothing has been entered. |
number | Text input, accepting numbers only | The label that should be shown above the number input supplied as a Dictionary. | The numeric user input as a string or an empty string if nothing has been entered. |
obfuscated-number | Numeric input for sensitive data. Should only accept numbers and obfuscate them by default unless the user toggles them to be shown. Should not use system keyboard, dictionaries or auto-correct features. | The label that should be shown above the number input supplied as a Dictionary. | The user input as a string or an empty string if nothing has been entered. |
email | Text input for entering an email. | The label that should be shown above the email input supplied as a Dictionary. | The user input as a string or an empty string if nothing has been entered. |
| Markdown text field | text | – | Shows a static text to the user. | The text that should be shown, supplied as a Dictionary. The text may contain basic markdown elements like bold, emphasis or links. | – |
| Option field | option | button | A button or a set of buttons. If a button is pressed by the user the form is submitted. Having buttons in the form automatically hides the submit-button. Default if format is not specified or not supported. | The labels, divided by \n, to be shown on the buttons supplied as a Dictionary. | The numeric, zero-based position of the picked button in the provided array as a string. |
| Payment card field | paymentcard | – | The label shown next to the input field supplied as a Dictionary. | Payment card information as number, expiration date and CVV code | A PAN validated with the Luhn algorithm. The “cvv” field might be optional depending on Service Provider Configuration, then it can be left empty. JSONObject: { "cardNumber": "XXXXXXXXXXXXXXXX", "expiryMonth": Int, "expiryYear", Int, "cvv", "XXX" } |
Data validation
The application that the user is using is expected to validate the context to at least match the expected return format and size as per the above table.
API
The Service Provider should POST a JSON formatted request to the /userInteraction endpoint similar to the following structure:
{
"fields": [{
"label": {
"en": "English label",
"se": "Swedish label"
},
"id": "any_field_id",
"type": "edit",
"format": "number"
...
}],
"encrypted": "false"
}Result
The userInteraction request will yield an operationId and UUID. After some time (the user is filling in the required information) the Service Provider will receive the ID of the operation, a status code and the results. The result will be in JSON and formatted like for example:
{
"operationId": "0276F6A6-E21C-4307-B63C-1F70D6C36045",
"sessionId": "C4D14B40-8F1C-456C-A7E2-4069B5F8CBBC",
"statusCode": 200,
"fields": {
"any_field_id": "field_string_value"
}
}Encryption
It is possible to specify that the data submitted by the user travels encrypted from the mobile client to the Service Provider, so that sensitive data such as payment card details cannot be compromised.
Encrypted user interactions are done with a combination of symmetric and asymmetric encryption. An ephemeral AES key is generated by the client and used to encrypt the /userInteraction data. Then, this key is encrypted with the public key of the Service Provider. The client returns the ephemeral-key encrypted data, and the public-key encrypted ephemeral key. Upon receival, the Service Provider decrypts the ephemeral key with its private key, and then, with the newly decrypted ephemeral key, decrypts all the data.
To activate encryption the Service Provider needs to pass a public key as a certificate along with the service description:
{
"title": "The encrypted userInteraction service",
"description": "This is an encrypted userInteraction service.
Keep out of reach from children.",
...
"certificate": [A X.509 certificate encoded as ASN1.DER]
}To encrypt a /userInteraction the Service Provider must also set the encrypted flag to true like for example:
{
"fields": [{
"label": {
"en": "English label"
},
"id": "any_field_id",
"type": "edit",
"format": "number",
...
}],
"encrypted": "true"
}The encrypted data together with the encrypted ephemeral key will be sent back as previously described in the Result section but with the fields being encrypted and the additional field "ephemeralKey":
{
"operationId" : "0276F6A6-E21C-4307-B63C-1F70D6C36045",
"sessionId" : "C4D14B40-8F1C-456C-A7E2-4069B5F8CBBC",
"statusCode": 200,
"fields": {
"any_field_id": [byte array in a hex form]
},
"ephemeralKey": [byte array in a hex form]
}The "ephemeralKey" is encrypted using RSA/OAEP algorithm with a SHA512 for hashing and MGF1 Padding (RSA/NONE/OAEPWithSHA512AndMGF1Padding). To obtain field data one needs to decrypt the "ephemeralKey" first and then using the obtained key to decrypt each field separately using AES/CBC algorithm with a PKCS7 padding (AES/CBC/PKCS7Padding). As initialization vector an array with 16 zero bytes can be used.